Analyzing KaiXin Exploit Kit
First
Yesterday, the activity of KaiXin Exploit Kit has been reported by Brad.http://malware-traffic-analysis.net/2017/11/17/index.html
I began learning about EK from February 2017. Therefore, I didn't know about KaiXin EK, so I tried to analyze.
What is KaiXin Exploit Kit
According to "Recent example of KaiXin exploit kit", KaiXin EK has been observed since August 2012. It's mainly used for attack campaign targeting China, and in recent years almost no activity has been reported. What kind of mechanism is attacking?Traffic Chain
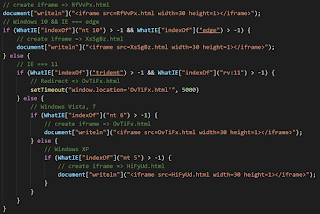
First, I briefly introduce the chain of traffic generated by KaiXin EK. Please look at the images.When accessing KaiXin EK's landing page, multiple attack codes are loaded. The attack code branches depending on the user's environment (IE, JRE, Flash Player version, etc). Ultimately, if the user is an attack target, malware (exe file) will be downloaded and executed.
Lansing Page
KaiXin EK obfuscates JavaScript including attack code. Landing page is also obfuscated, but very simple. When decrypting according to the flow, the following code is obtained.https://gist.github.com/koike/5fe67c5c608ef76f735119be8f6e7f79
Using the version information of JRE or IE, branch the next processing.
For example, if JRE version is between 17006 and 17011, load Java Applet "EyDsJd.jar". At that time, malware ("11.7.exe") URL is passed as argument, and jar downloads and executes that malware by exploiting the vulnerability of JRE.
The vulnerabilities used by each jar files are these.
BvJfRc.jar CVE-2012-4681
EyDsJd.jar CVE-2013-0422
XlGaYb.jar CVE-2011-3544
After that, EK uses vulnerabilities other than JRE.
Let's look at each of the html files that are being loaded.
RfVvPx.html
"RfVvPx.html" is always loaded. It attacks Adobe Flash Player vulnerabilities.https://gist.github.com/koike/d958b5ea79a558e5f440008d2abc1ae7
Use the version information of Flash Player and IE to change the swf file to be loaded. I don't know swf, but EK downloads and executes malware using some Adobe Flash Player's vulnerability.
XsSgBz.html
"XsSgBz.html" is loaded when user is using Edge on Windows 10. This html attacks CVE-2016-7200 and CVE-2016-7201. This vulnerability was used in multiple EKs. Details are described on Kafeine's blog.http://malware.dontneedcoffee.com/2017/01/CVE-2016-7200-7201.html
The first part contains the code to decode the URL of the download destination and the shellcode to download and execute the malware.
https://gist.github.com/koike/01bea2bcd1ec805d4fc67a2514e95aef
shellcode is published in github below.
https://github.com/stephenbradshaw/shellcode/blob/master/descript.asm
The second part is an exploit for Microdoft Edge. (CVE-2016-7200 and CVE-2016-7201). Just deleting comments etc. will almost match the code published on the following github page.
https://github.com/theori-io/chakra-2016-11/blob/master/exploit/FillFromPrototypes_TypeConfusion_NoSC.html
OvTiFx.html and HiFyUd.html
"OvTiFx.html" and "HiFyUd.html" use CVE-2016-0189. This vulnerability is also used in RigEK and others. For details, please see here.https://gist.github.com/koike/7aae4bdd11cd415c83f2cea4cddc9d03
Malware
This malware is used by KaiXin EK. I cannot identify this. Please tell me if you can analyze.MD5 : 1a1929f525a710c81dfb7873ddad9d33
SHA256 : f710f3c77276e7082d68d365413a658d80b6cac66c8b0c9a67b20426259a2035
https://www.hybrid-analysis.com/sample/f710f3c77276e7082d68d365413a658d80b6cac66c8b0c9a67b20426259a2035?environmentId=100
https://www.virustotal.com/#/file/f710f3c77276e7082d68d365413a658d80b6cac66c8b0c9a67b20426259a2035/detection
Finally
KaiXin EK didn't have much complicated mechanism, but logic was interesting. The vulnerabilities used by EK are old and not very strong, but I enjoyed the analysis ;)Zip archive of the IOC files is here
https://gist.github.com/koike/276628c896f572a7ebc9e0b933d27c78
 nao_sec
nao_sec